Sometimes, if you are a computer security enthusiast or are curious about some incidents, you will have to carry out your investigations from places where you may not have access to your laboratory or just prefer to use tools that are available in the cloud. If this is the case, this article compiles the main and its different purposes.
# 1 Network Tools
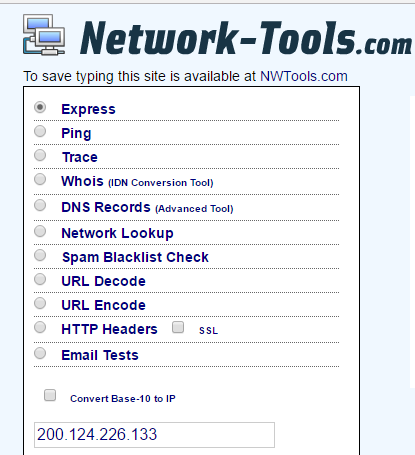
This type of tool is used a lot to obtain information on a particular domain or IP address, from whom the registration, who owns it, the country where it is located and even information of the Hosting service, which can be very useful, to request cancellation of a C & C site or phishing .
Other similar portals can also indicate which domains are stored in the same IP address. This valuable information could be useful in detecting, for example, from which domain a web server could be compromised.
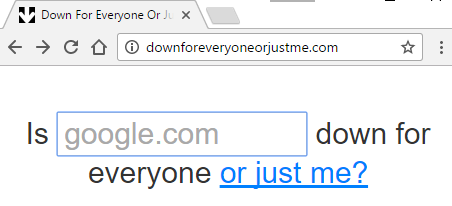
# 2 Down for everyone or just me
Maybe at some point you are not sure if a site is active or not, although you can see it. This behavior is relatively common, since in many cases it is possible that the site in question is stored in different places, as an example in the cache of your browser.
This small portal will clear your doubts very simply. You must enter the URL of the domain to analyze in the blank space:
# 3 Proxies
From the laboratories of ESET Latin America we have analyzed threats that act in different ways depending on the IP address or geolocation of the victim. In cases of this type, using some IP, you can observe behaviors emulating different locations:

# 4 Decoders
In the analysis of malicious code we naturally find code obfuscated or codified with various algorithms. To see more clearly you could write a few lines in Python or use Code Beautify , which will be of great help.
# 5 Sandboxes
These tools are sometimes very useful for running a suspicious application and giving you an idea of how it works. However, it is true that they do not always work, because some of these detect the sandboxes and do not run, to prevent their study. Techniques using some reverse engineering to cancel that part of the code, we can observe their behavior when running within the sandbox , which will give us valuable information as modified or created files, registry keys added, persistence, connections, etc.
# 6 Virus Radar
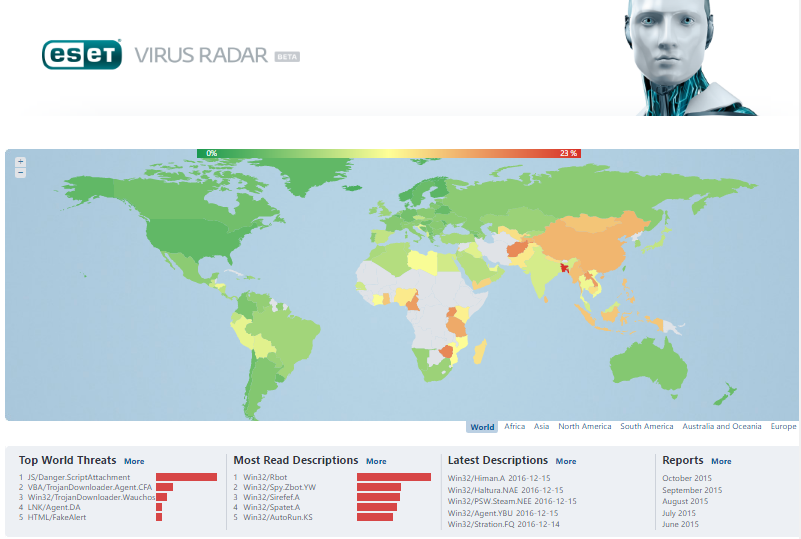
This free ESET service provides detailed statistics on malicious code based on detections of their security solutions installed in different Internet providers around the world participating in the project. Using these statistics, it is possible, among other things, to know the growth of epidemics of new viruses, as well as their life cycle, and to relate detections with geographic locations.
# 7 Social Networking
Although in many cases social networks are associated with leisure activities, for technical issues there are specific communities that generate forums or thematic discussion groups. These virtual rooms are used to debate or share solutions that will help overcome technical problems or various concerns that are shared. A clear example is observed through the groups of LinkedIn, as we see in the following image:
There are also other social networks, specialists and users who share videos and tutorials about computer security, as in the case of Security Tube .
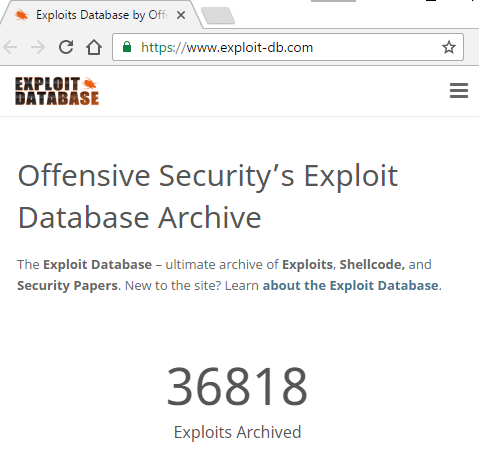
# 8 Exploit DB
In most offensive investigations surely be very useful to find some exploit to achieve an intrusion through any vulnerability found. In many cases, this may not be a simple task, but in this large database and find all the necessary materials including tutorials, shellcodes and even 0-days . Remember that these tools should be used under the principles of ethical hacking and never for malicious purposes.
# 9 VirusTotal
This website provides free analysis of files and web pages through different antivirus. If you have a suspicious file, this system uses about 55 antivirus and 61 online scan engines for analysis. In addition, it will inform the hash of the file, if another user has previously uploaded the same executable, and there is even the possibility to leave comments.
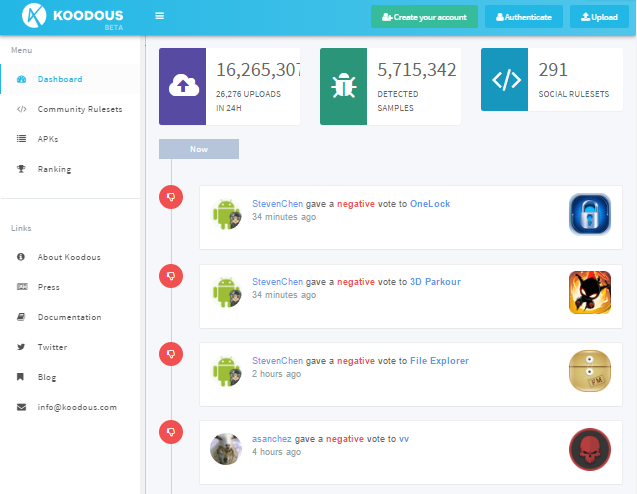
# 10 Koodous
This platform was designed for the community study of malware on mobile devices, analogously to VirusTotal. The developers showed up at Black Hat, where, in addition to explaining its operation, said that they had already analyzed more than 13 million applications, of which more than 4 million were infected by some type of malware. This gives us an idea of the size of your database and the potential value of this information.
These are just some of the thousands of tools that are available on the Internet. Through search engines such as Shodan for the Internet of Things or techniques Google Hacking , you’ll also find interesting results.
Fuente:https://www.welivesecurity.com/

Entusiasta de la seguridad cibernética. Especialista en seguridad de la información, actualmente trabajando como especialista en infraestructura de riesgos e investigador.
Experiencia en procesos de riesgo y control, soporte de auditoría de seguridad, diseño y soporte de COB (continuidad del negocio), gestión de grupos de trabajo y estándares de seguridad de la información.
Envía tips de noticias a info@noticiasseguridad.com o www.instagram.com/iicsorg/.
También puedes encontrarnos en Telegram www.t.me/noticiasciberseguridad