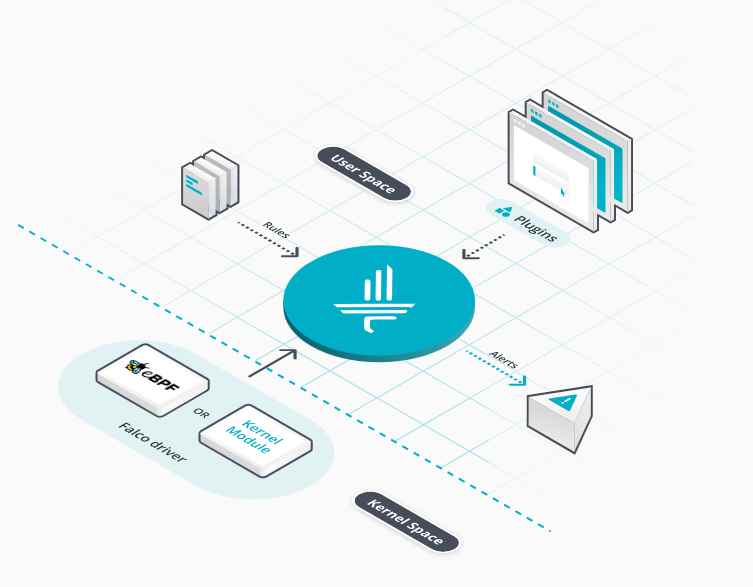
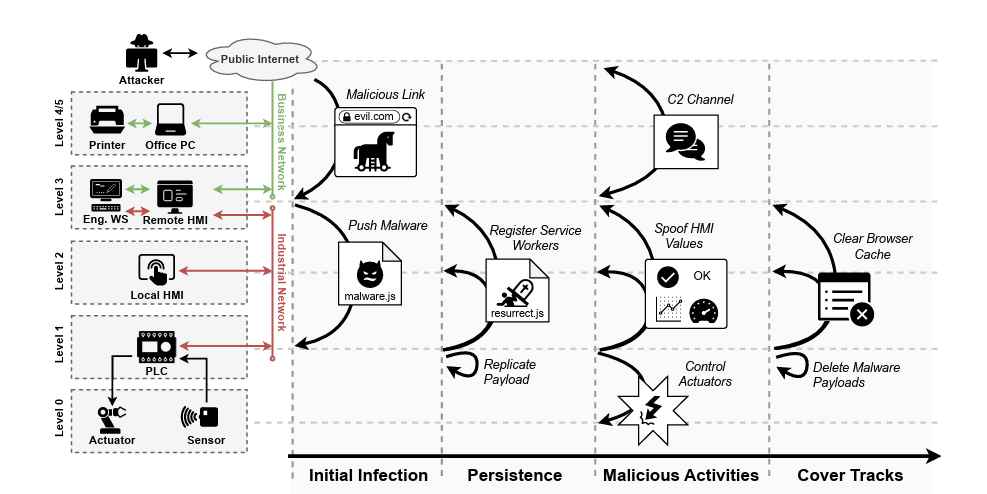
The BlackEnergy malware is crimeware turned APT tool and is used in significant geopolitical operations lightly documented over the past year. An even more interesting part of the BlackEnergy story is the relatively unknown custom plugin capabilities to attack ARM and MIPS platforms, scripts for Cisco network devices, destructive plugins, a certificate stealer and more. Here, we present available data – it is difficult to collect on this APT. We will also present more details on targets previously unavailable and present related victim profile data.
These attackers are careful to hide and defend their long-term presence within compromised environments. The malware’s previously undescribed breadth means attackers present new technical challenges in unusual environments, including SCADA networks. Challenges, like mitigating the attackers’ lateral movement across compromised network routers, may take an organization’s defenders far beyond their standard routine and out of their comfort zone.
Source:https://securelist.com/blog/research/67353/be2-custom-plugins-router-abuse-and-target-profiles/

Trabajando como arquitecto de soluciones de ciberseguridad, Alisa se enfoca en la protección de datos y la seguridad de datos empresariales. Antes de unirse a nosotros, ocupó varios puestos de investigador de ciberseguridad dentro de una variedad de empresas de seguridad cibernética. También tiene experiencia en diferentes industrias como finanzas, salud médica y reconocimiento facial.
Envía tips de noticias a info@noticiasseguridad.com o www.instagram.com/iicsorg/
También puedes encontrarnos en Telegram www.t.me/noticiasciberseguridad