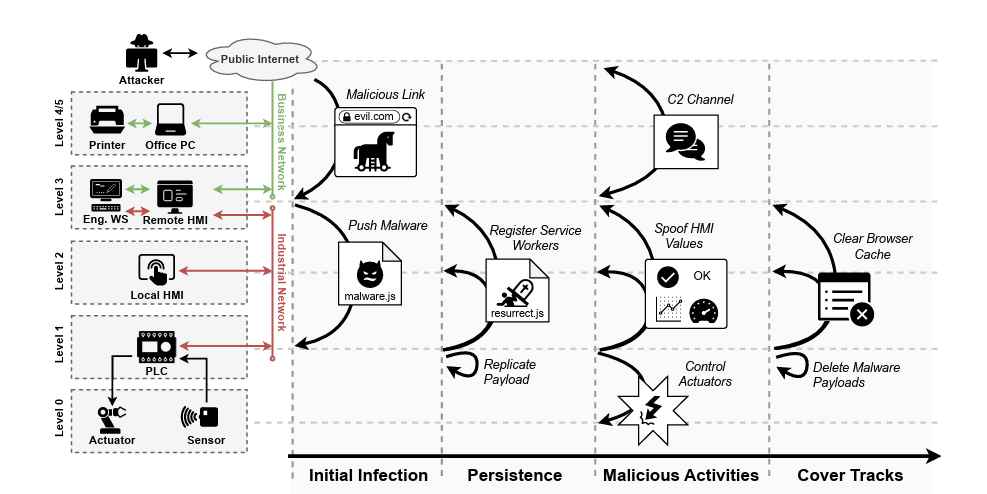
Isolating a sensitive computer network from the Internet can be an efficient security measure, but threat actors have found ways to get around it. A group believed to be linked to the Russian government, know as “Sednit,” “APT28” and “Sofacy,” appears to have developed the tools necessary to achieve this task.
In a recent report on the attacks launched by APT28 against European governments, militaries and security organizations, FireEye revealed that one of the tools used by the group is a modular family of implants called CHOPSTICK. Researchers identified one variant of CHOPSTICK that defeats closed networks by routing messages between local directories, the registry and USB drives.
Source:https://www.securityweek.com/attackers-using-usb-malware-steal-data-air-gapped-networks

Trabajando como arquitecto de soluciones de ciberseguridad, Alisa se enfoca en la protección de datos y la seguridad de datos empresariales. Antes de unirse a nosotros, ocupó varios puestos de investigador de ciberseguridad dentro de una variedad de empresas de seguridad cibernética. También tiene experiencia en diferentes industrias como finanzas, salud médica y reconocimiento facial.
Envía tips de noticias a info@noticiasseguridad.com o www.instagram.com/iicsorg/
También puedes encontrarnos en Telegram www.t.me/noticiasciberseguridad